Keeping sensitive data and configuration data under control is essential for applications to run smoothly in the complicated world of Kubernetes. Two key Kubernetes resources that help developers effectively manage configurations and sensitive data are ConfigMaps and Secrets.
What do Kubernetes ConfigMaps and Secrets mean?
Key-value pairs containing non-sensitive configuration data are stored in Kubernetes resources called ConfigMaps. By separating configuration artifacts from container images, they facilitate the management of application configuration. ConfigMaps can be accessible as environment variables in containers or mounted as volumes.
On the other hand, secrets are Kubernetes resources that are used to hold private data, like SSH keys, OAuth tokens, and passwords. They are designed to safely store sensitive data and are encoded as base64 strings. Like ConfigMaps, secrets can be exposed as environment variables in containers or mounted as volumes.
Why Use ConfigMaps and Secrets?
Separation of Concerns: By using ConfigMaps and Secrets, you can separate configuration data and sensitive information from application code, promoting a clean and modular architecture.
Enhanced Security: Secrets provide a secure way to store sensitive data, ensuring that passwords, tokens, and other confidential information are not exposed in plaintext.
Portability and Flexibility: ConfigMaps and Secrets are portable across environments, allowing you to manage configuration data and secrets consistently across development, staging, and production environments.
Dynamic Updates: ConfigMaps and Secrets can be updated dynamically without restarting containers, enabling seamless configuration changes and reducing downtime.
Task 1: Creating a ConfigMap for your Deployment
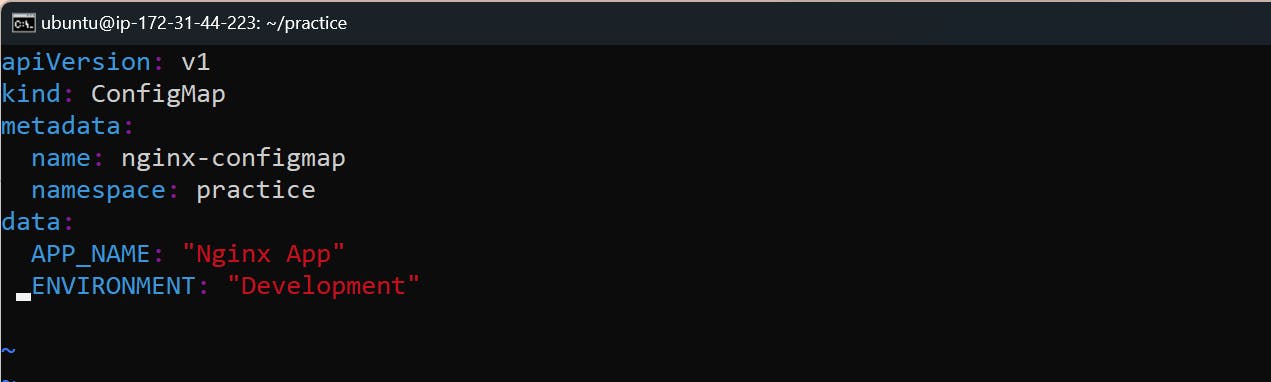
Step 1: Create a ConfigMap for your Deployment using a file.
apiVersion: v1
kind: ConfigMap
metadata:
name: nginx-configmap
namespace: practice
data:
APP_NAME: "Nginx App"
ENVIRONMENT: "Development"
Run the following command to create the ConfigMap:
kubectl apply -f configmap.yml -n practice
Step 2: Update the deployment.yml file to include the ConfigMap
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
namespace: practice
labels:
app: nginx
spec:
replicas: 3
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:1.14.2
ports:
- containerPort: 80
envFrom:
- configMapRef:
name: nginx-configmap
Apply the updated deployment by running the following command:
kubectl apply -f deployment.yml -n practice
This will apply the changes to the deployment and create the associated Pods.
Check the status of the deployment and ConfigMap by running the following command:
kubectl get deployment -n practice
kubectl get configmap -n practice
This will display the status of the deployment and ConfigMap.

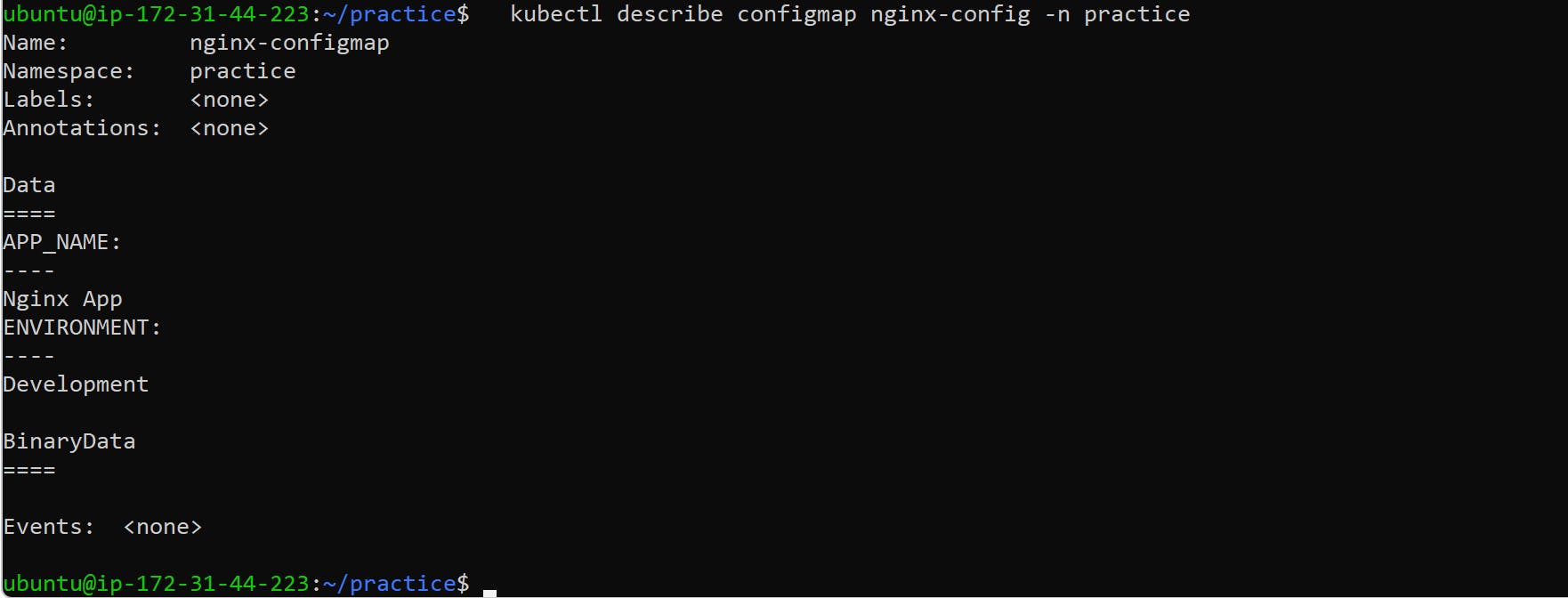
Use the describe command to get a detailed view of the ConfigMap.
kubectl describe configmap nginx-config -n practice
This will provide detailed information about the ConfigMap, including the data stored within it.
Navigate inside the Pod and check the environment variable and the application for detailed status.
kubectl exec -it <pod-name> -n practice-- shReplace
<pod-name>with the actual name of the Pod. This will give you access to the Pod's shell.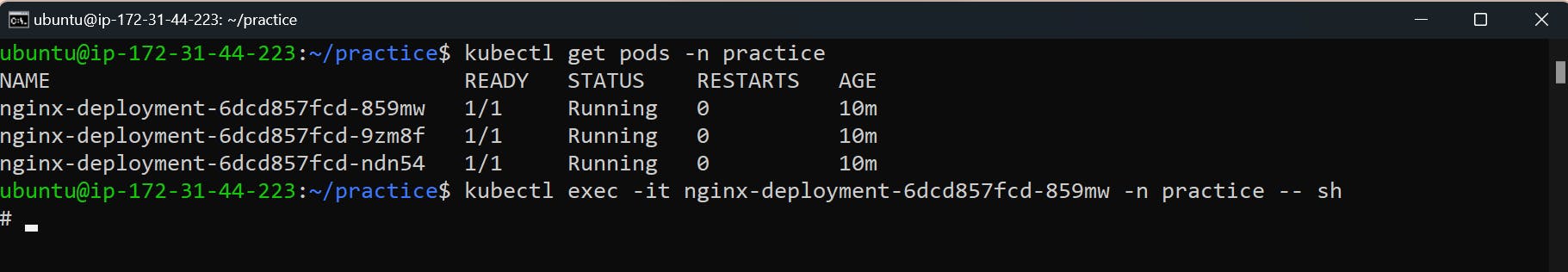
Inside the Pod, check the environment variables by running the following command:
envThis will display the environment variables, including the ones sourced from the ConfigMap.

In the output, we can find the env variables we've configured using the configmap, APP_NAME and ENVIRONMENT
Task 2: Creating a Secret for your Deployment
Step 1: Create a Secret secret.yml file and define the base64-encoded password.
apiVersion: v1
kind: Secret
metadata:
name: nginx-secret
namespace: practice
type: Opaque
data:
username: <base64-encoded-username>
password: <base64-encoded-password>
To add the password in the above file you need to generate the base64 encoded password.
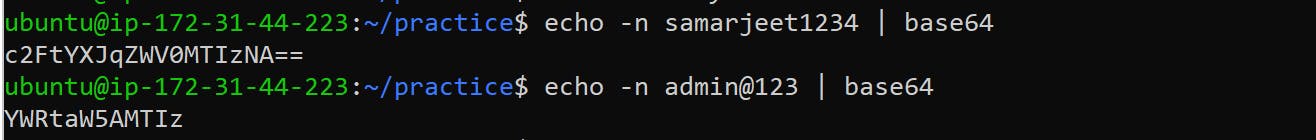
Run the following command to create the Secret:
kubectl apply -f secret.yml -n practiceThis will create the Secret named
nginx-secretin the practice namespace.Update the
deployment.ymlfile to include the Secret configuration. Add theenvfield under thecontainerssection of the deployment.
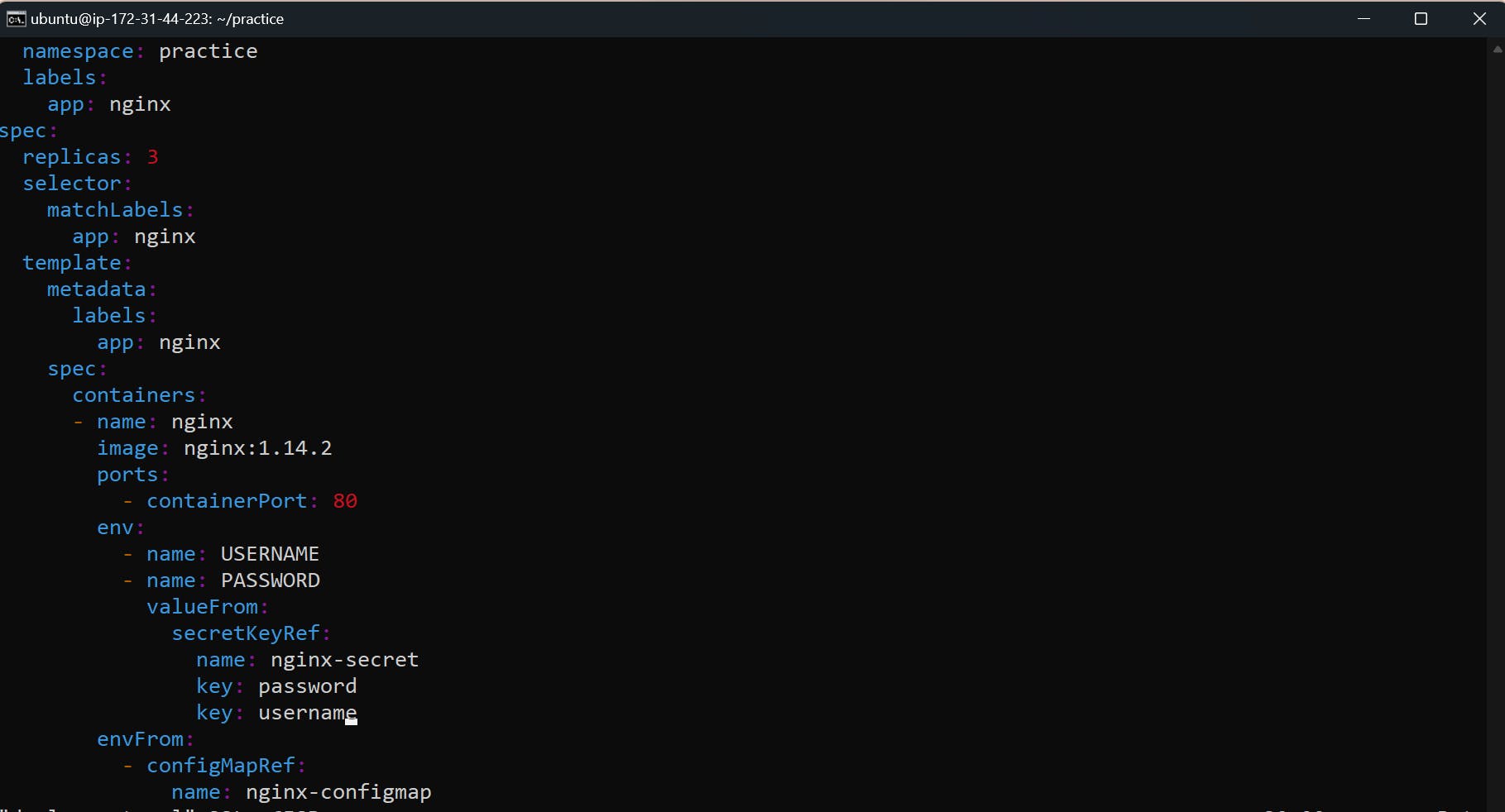
Apply the updated deployment by running the following command
kubectl apply -f deployment.yml -n practice
This will apply the changes to the deployment and create the associated Pods.
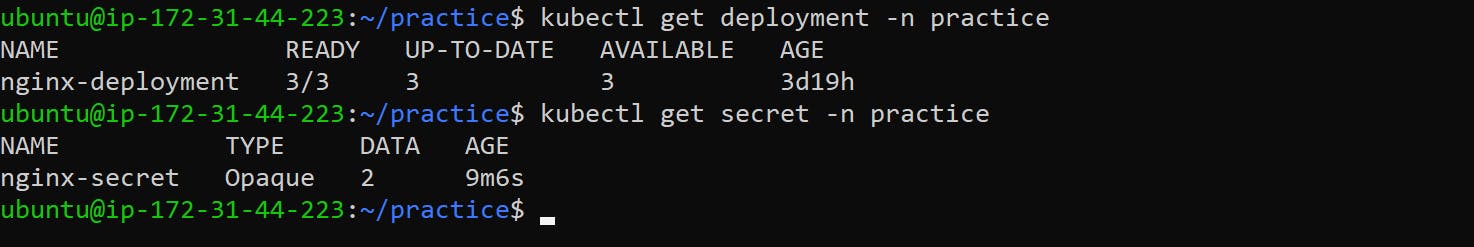
Check the status of the deployment and Secret by running the following command:
kubectl get deployment -n practice
kubectl get secret -n practice
This will display the status of the deployment and Secret.
Use the describe command to get a detailed view of the Secret:
kubectl describe secret nginx-secret -n practice
This will provide detailed information about the Secret.

Check the running Pods by running the following command:
kubectl get pods -n practice
Navigate inside a Pod associated with the deployment by running the following command:
kubectl exec -it <pod-name> -n practice -- shInside the Pod, view the environment variable by running the following command:
echo $PASSWORDThis will display the value of the
PASSWORDenvironment variable, which is sourced from the Secret.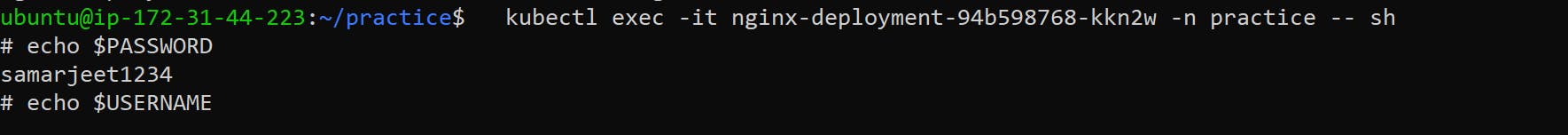
By mastering ConfigMaps and Secrets in Kubernetes, you can effectively manage configuration data and sensitive information, ensuring the security and reliability of your applications. With these powerful tools at your disposal, you can streamline your development workflow and build resilient containerized applications with ease.
Follow for more:
Linkedin: https://www.linkedin.com/in/samarjeet-patil-921952251/
#cloud #AWS #k8s #deployment #pods #yaml #sevice #networking #services #loadbalancer